To connect your Microsoft Entra ID to Kiro:
- Create Entra application for Kiro
- Configure Entra application
- Create the Kiro Profile
- Set Entra up application provisioning
- Add users and groups to Entra application
Step 1: Create an application for Kiro
First, create a new custom application in Microsoft Entra ID.
From the Microsoft Entra admin center create a new application (Enterprise applications -> New application). From the Microsoft Entra App Gallery select "Create your own application" option
Loading image...
Set a descriptive name, for example, Kiro-Entra. Then, select the "Integrate any other application you don't find in the gallery (Non-gallery)" option for the "What are you looking to do with your application?" field, and select "Create" to create the application.
Loading image...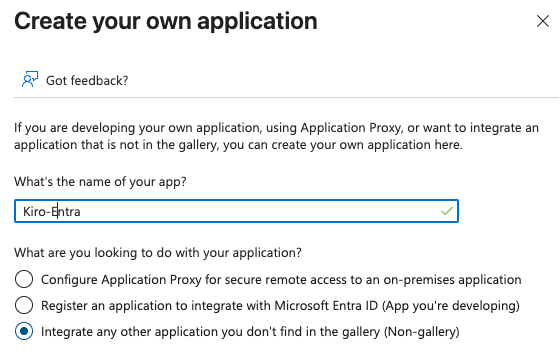
Step 2: Configure the Kiro application
Next, configure the application you have created to allow user identities to present the right authorization to access Kiro.
Expose API endpoint
Next, expose the API endpoint for Kiro to sync user identities.
For the "Kiro-Entra" application (App registrations -> All applications -> Kiro-Entra), select the "Expose an API" option. Select the "Add" link next to the "Application ID URI" field. This will bring up a dialog with a default value for the Application URI. Save it with the default value. Next, you have to add two scopes, that define the permissions that an identity has to present to Kiro for it to successfully respond to requests.
Loading image...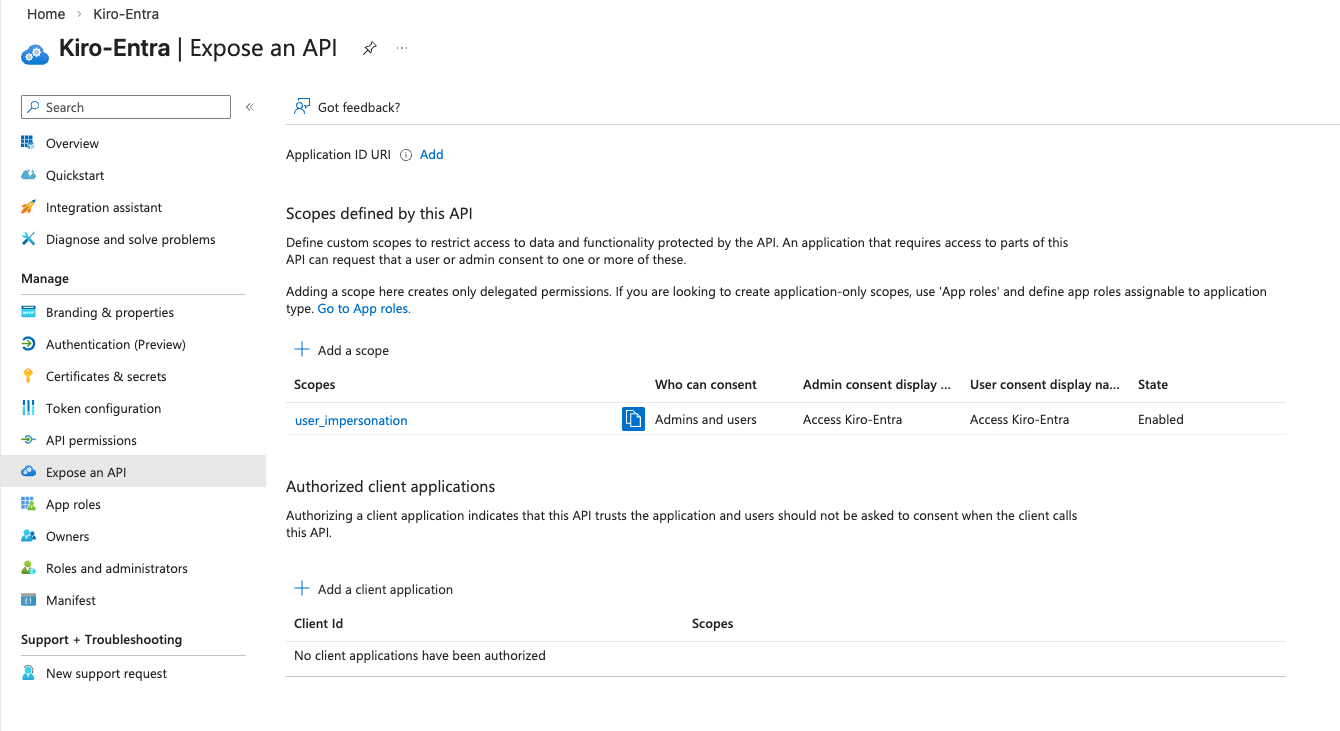
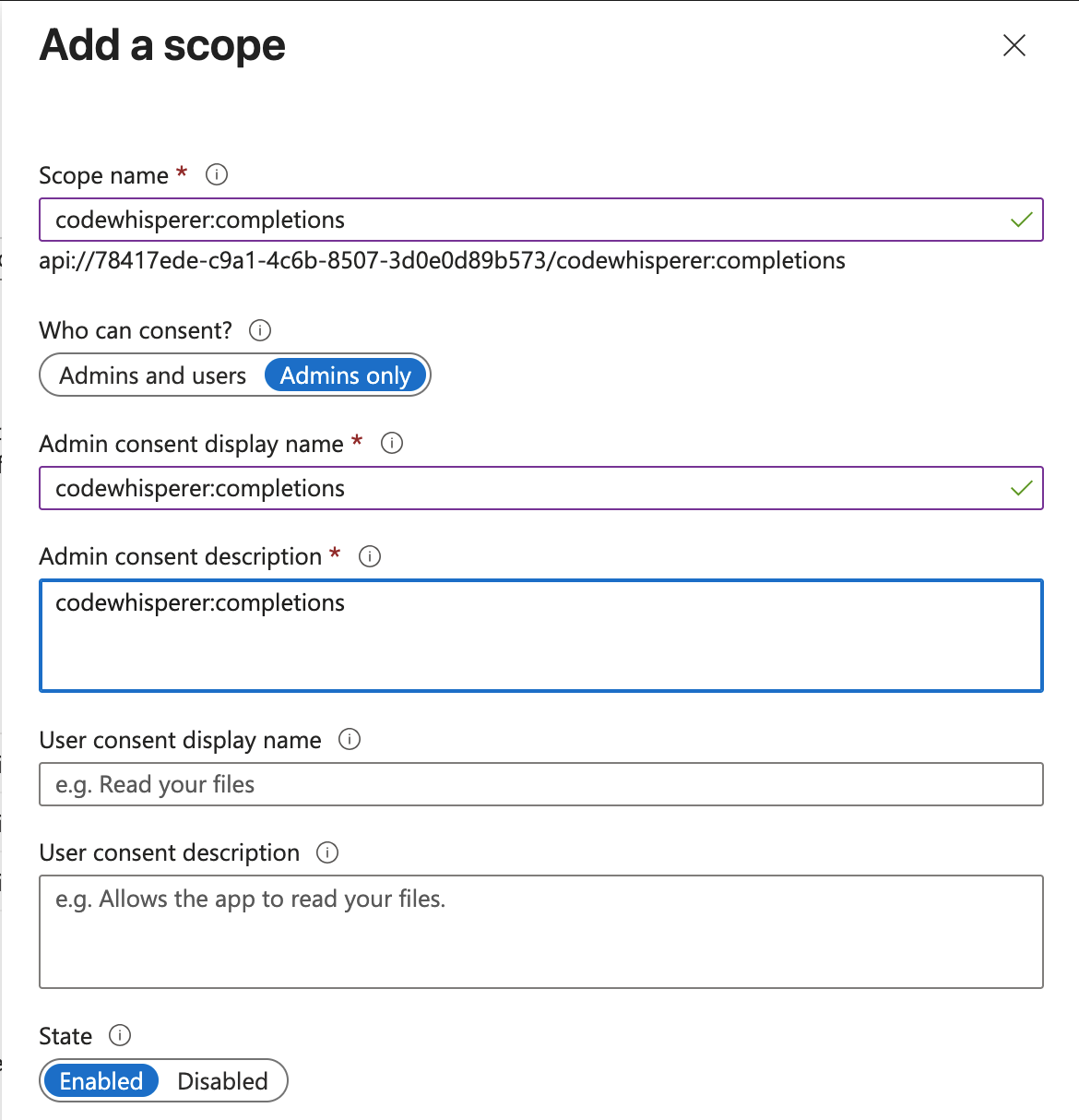
The first scope will enable users to have access to auto complete feature in Kiro by setting the following attributes of the scope:
- Scope Name: codewhisperer:completions
- Who can consent?: Admins and Users
- Admin consent display name: codewhisperer:completions
- Admin consent description: codewhisperer:completions
- State: Enabled
The second scope will enable users to have conversations with Kiro by setting the following attributes of the scope:
- Scope Name: codewhisperer:conversations
- Who can consent?: Admins and Users
- Admin consent display name: codewhisperer:conversations
- Admin consent description: codewhisperer:conversations
- State: Enabled
After you have completed adding the scopes, "Expose an API" page should look like this:
Loading image...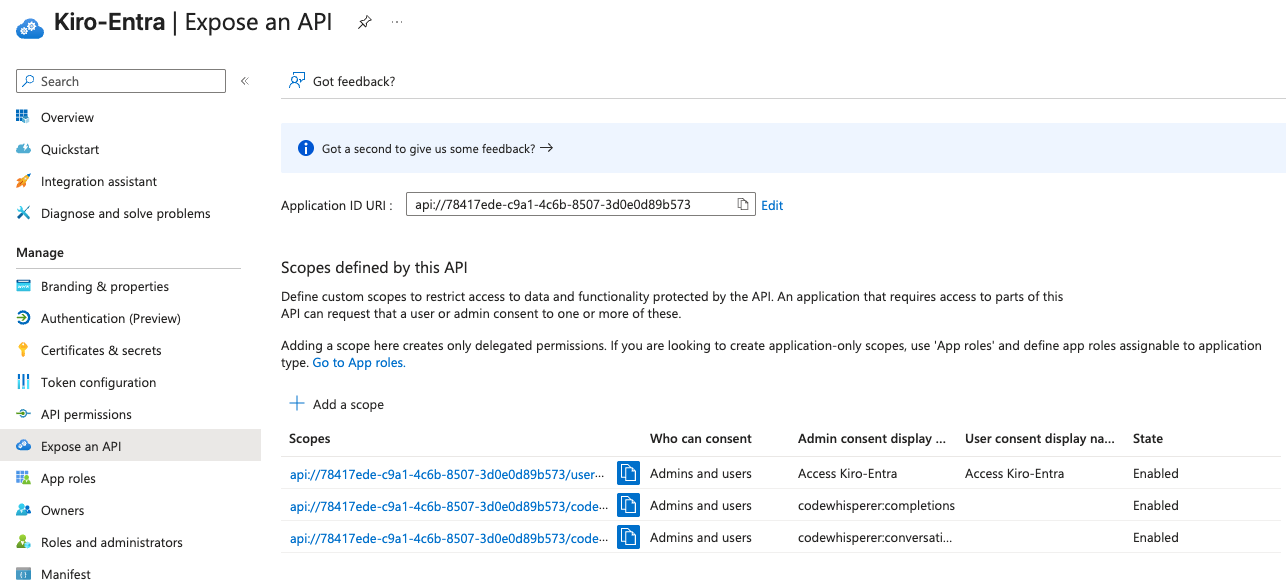
Add a redirect URI
Next, configure the URI of the Kiro clients to redirect from Microsoft Entra ID after the user completes authentication process. To do that, select "Authentication (Preview)" option for the Kiro application (example: Kiro-Entra). Select "Add Redirect URI" button and in the platform to set redirect URI select "Mobile and desktop application".
After adding the redirect URI, the page should look like this:
Loading image...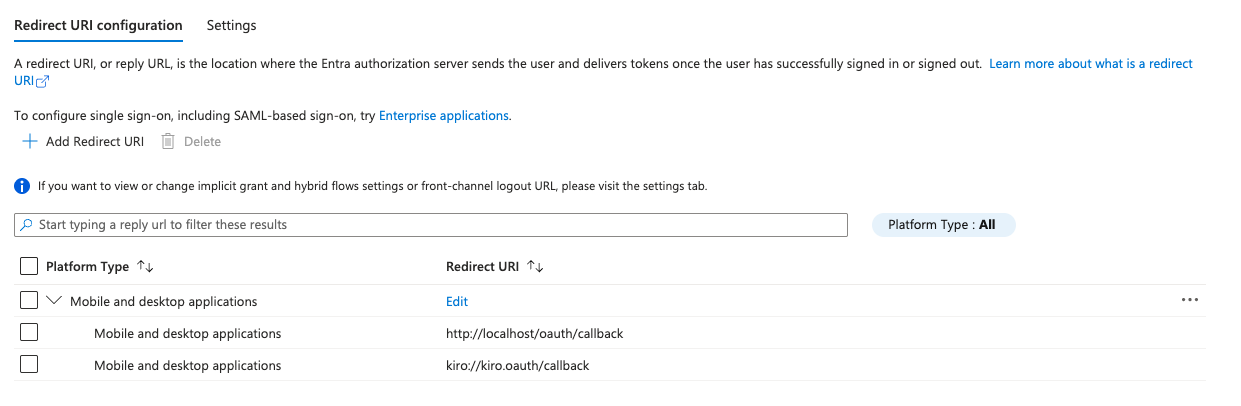
Set Access Token version
Last, set the version of the access token that Kiro will request. By default, Entra ID uses OAuth 1.0. Kiro expects OAuth 2.0. To do that, set the value of "api" → "requestedAccessTokenVersion" field to 2, and Save.
Loading image...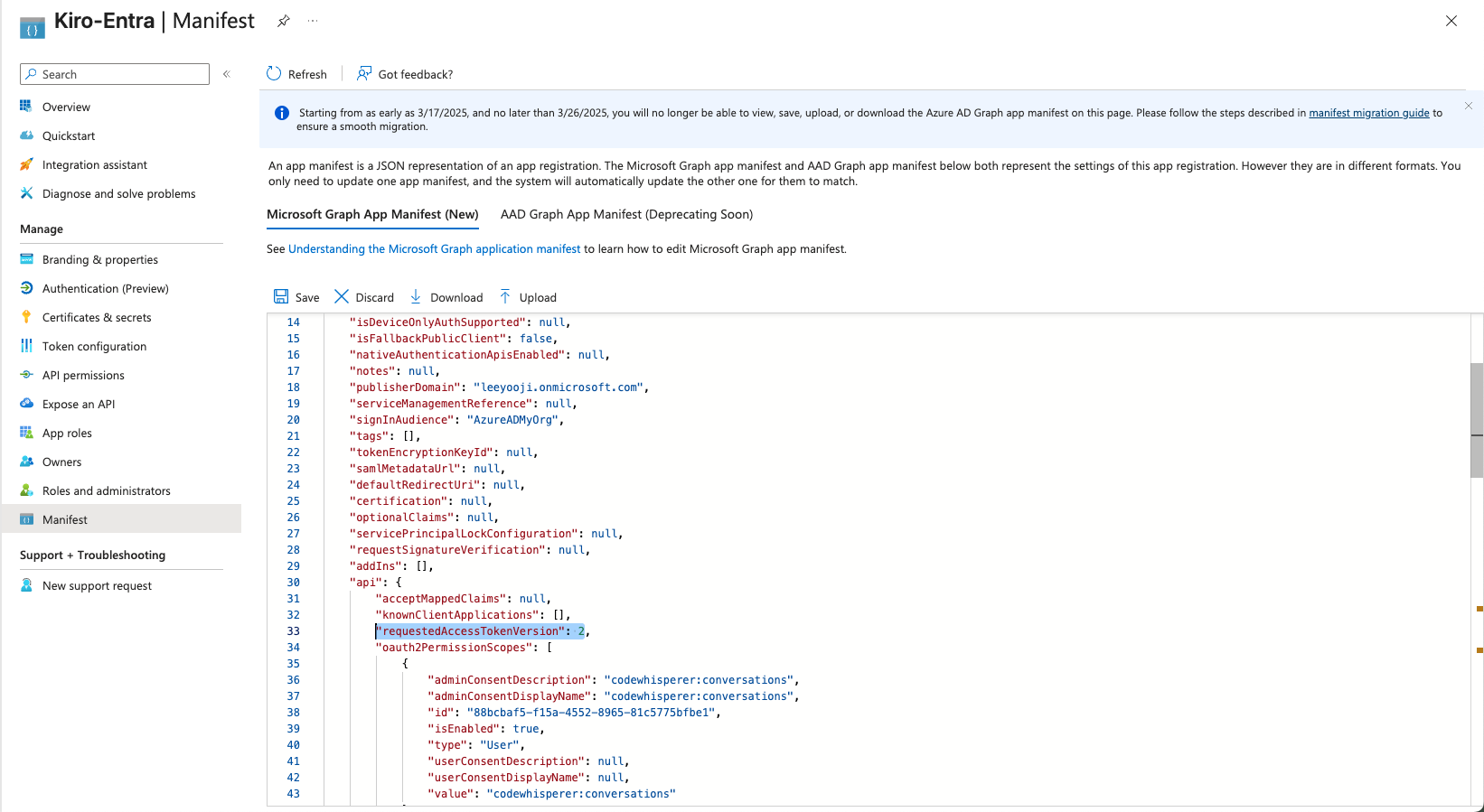
Now, you are ready to set up the Kiro Profile.
Step 3: Set up Kiro Profile
Setting up Kiro profile and connecting to your Microsoft Entra ID IdP consists of the following steps:
- Configuration Microsoft Entra ID application properties in Kiro
- Add and verify your domain in Kiro
- Set up provisioning in Microsoft Entra ID
- Verify Connection
Create the Kiro profile
In AWS console, navigate to the Kiro console and select "Get started" to set up a Kiro profile. Select "Connect an existing Identity provider" option to connect to Microsoft Entra ID.
Loading image...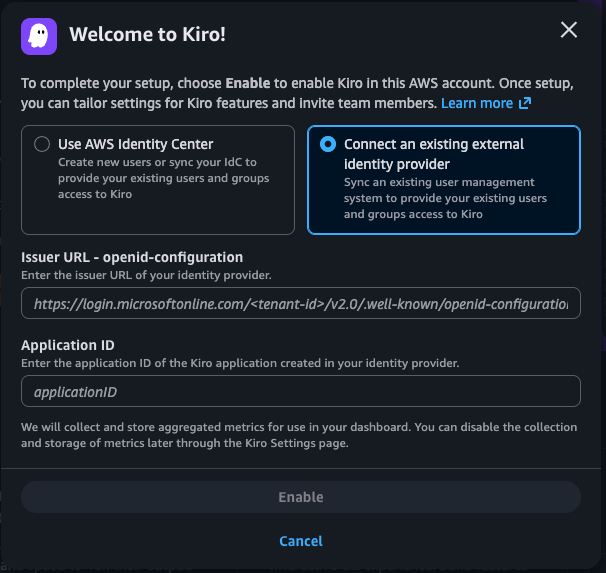
From the left nav in Microsoft Entra, select App registrations -> All applications and select "Kiro-Entra". In the "Overview" tab of the application, select "Endpoints". You will see a panel displayed with several endpoint URLs.
Loading image...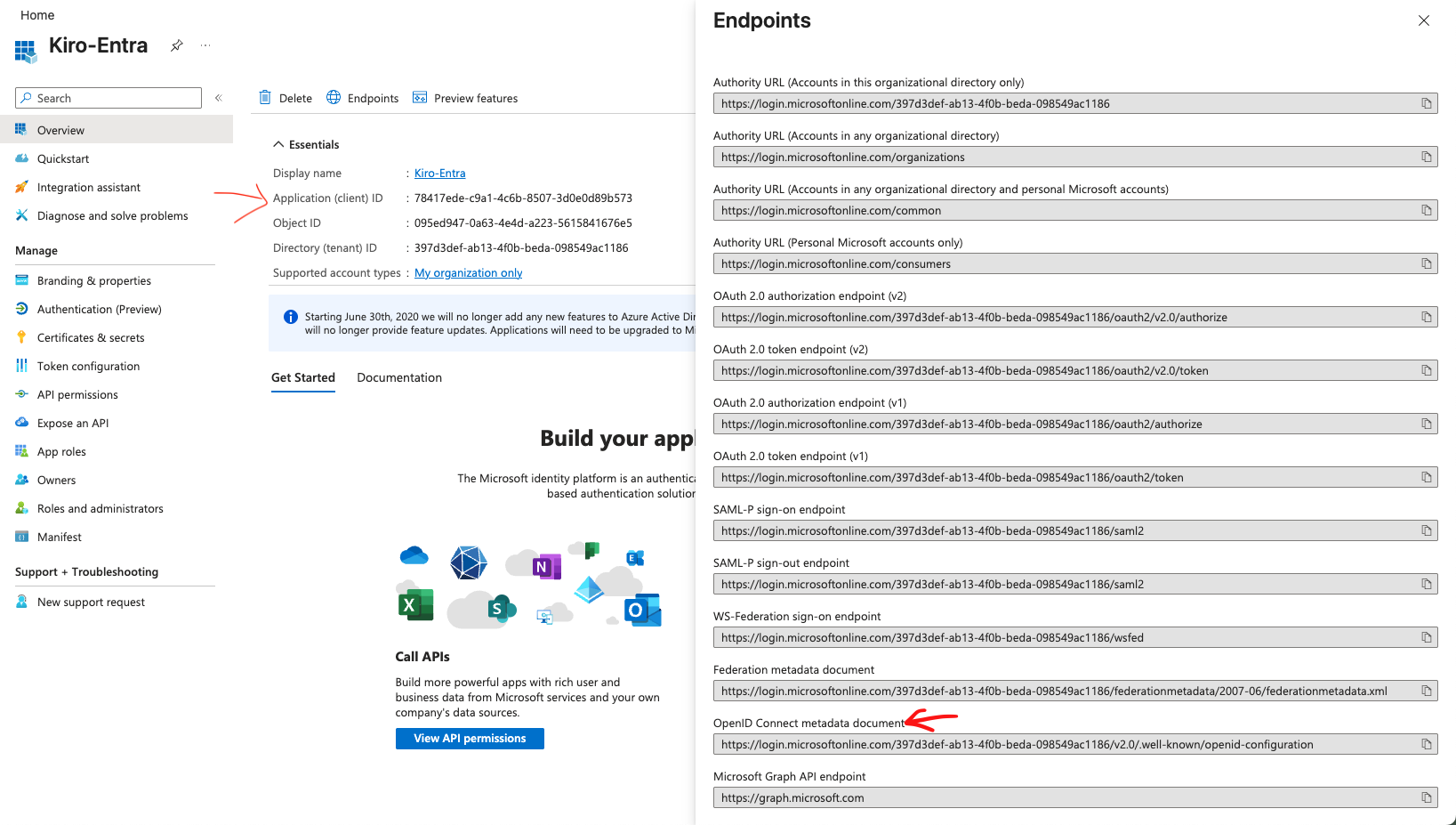
First, paste the value from "OpenID Connect metadata document" into the "Issuer URL" field in the Kiro Profile you are creating, and the value from "Application (client) ID" into the "Application ID" field in the Kiro Profile, and select "Create" to create the Profile.
Add and verify domain
Select the "Settings" button and in the Identity management -> Domains section, select "Add domain" to add your company domain
Loading image...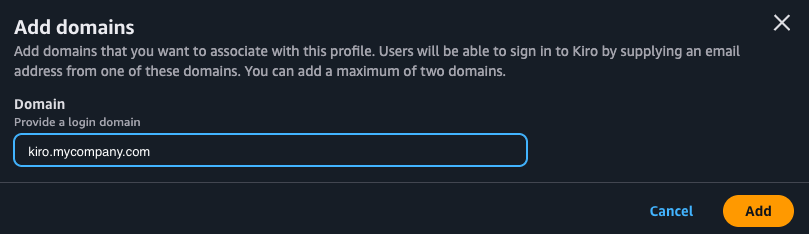
Selecting "Add" will add the domain and show you a verification token. Copy the verification token. The domain added will show up in the Domains list with "Pending" status.
In your DNS Provider like Amazon Route53, create TXT record with that verification token.
Loading image...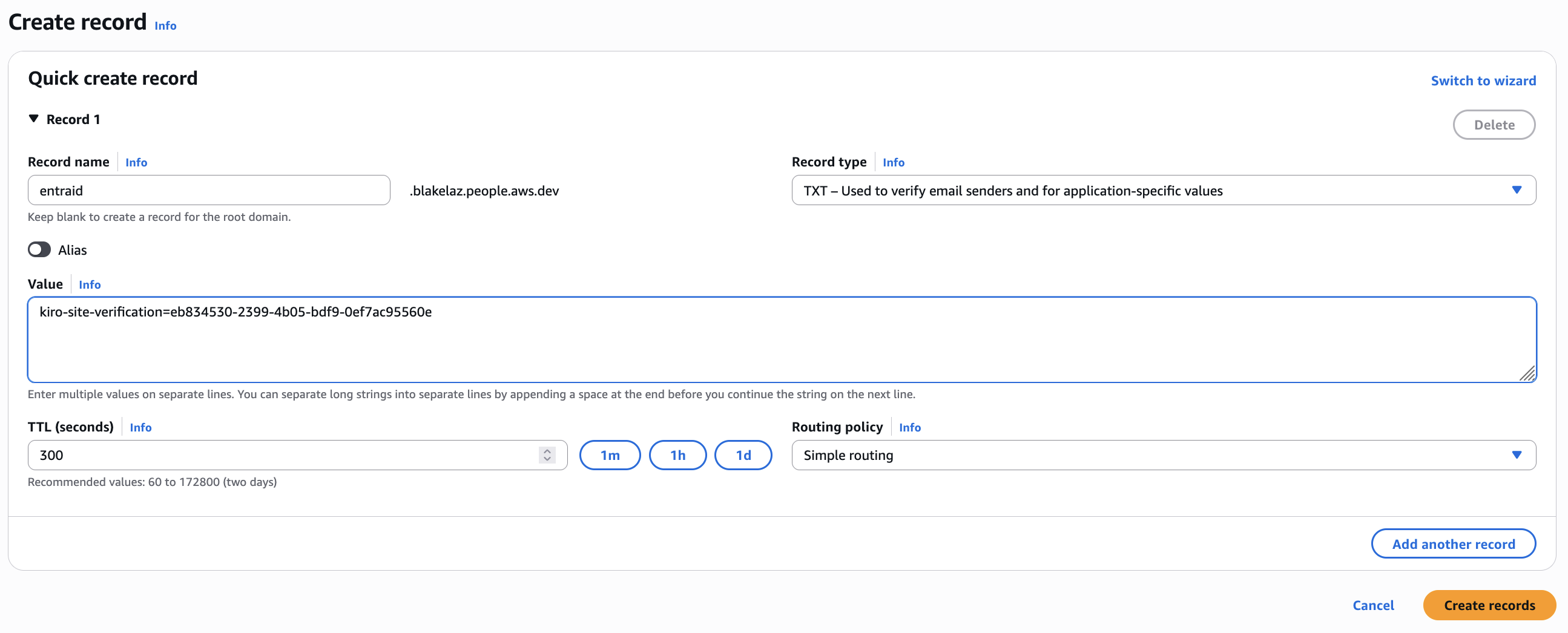
If the configuration is valid, after a few minutes the status will be "Verified".
Loading image...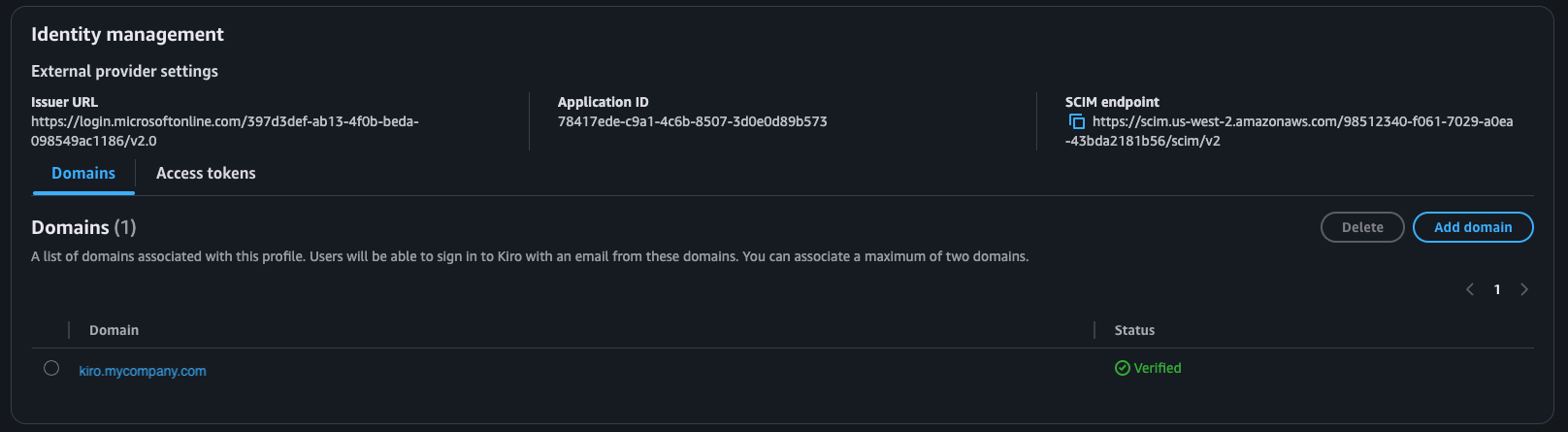
Step 4: Set up provisioning
In this step, you will provision the Kiro application and verify that Kiro can sync identities from your Entra ID identity store.
In Entra ID admin console, navigate to Enterprise Apps -> Kiro-Entra -> Provisioning. Select the "Provisioning" link from the side bar to configure the provisioning settings.
First, set the "Provisioning Mode" to Automatic. Next, you have to configure the Tenant URL and Secret token.
Loading image...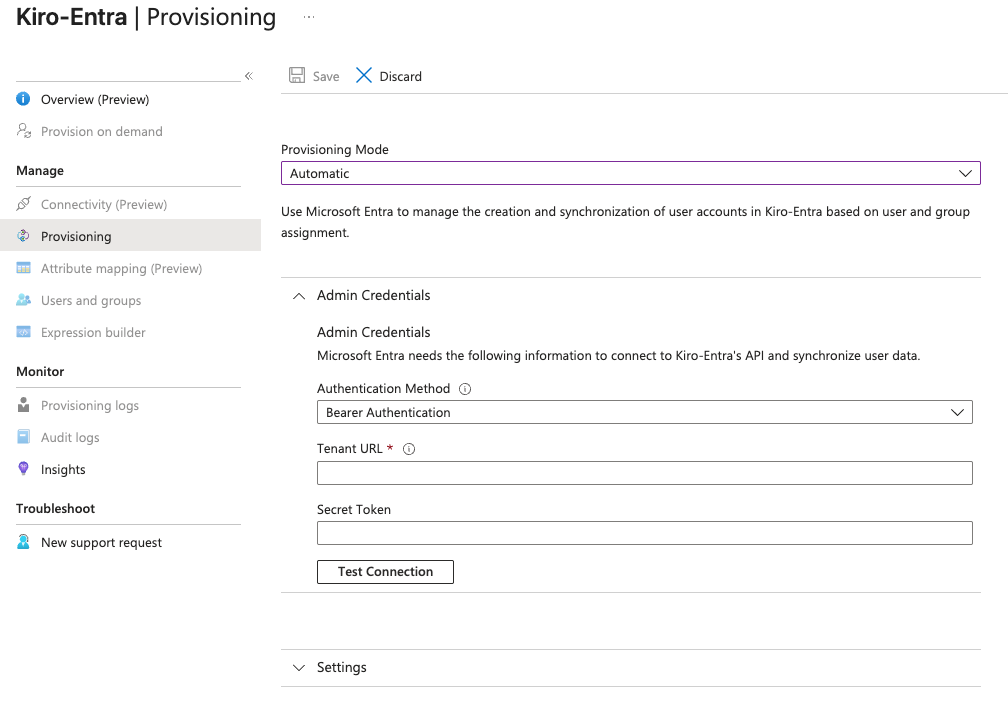
In the Kiro AWS console, navigate to Settings -> Identity Management -> Access Tokens section. Select "Generate Token" to generate an access token. Copy the access token and paste it in the "Secret Token" field in the Provisioning configuration.
Next, from the Settings page of the Kiro profile in the AWS console, copy the value in "SCIM Endpoint" from the "Identity management" section. Paste that in the "Tenant URL" field in the Provisioning configuration in Entra ID. With this, you have set up the secure synchronization of identities to Kiro from Entra ID.
Loading image...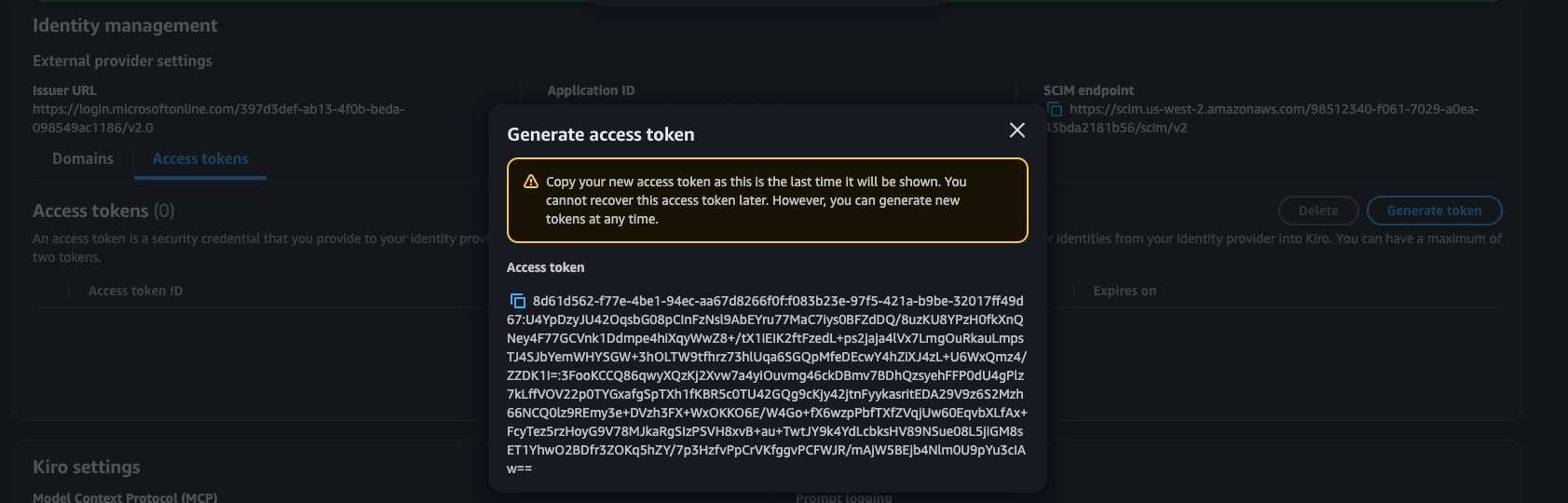
Now select "Test Connection" to validate the configuration. If that is successful, select "Save" to complete the provisioning.
Loading image...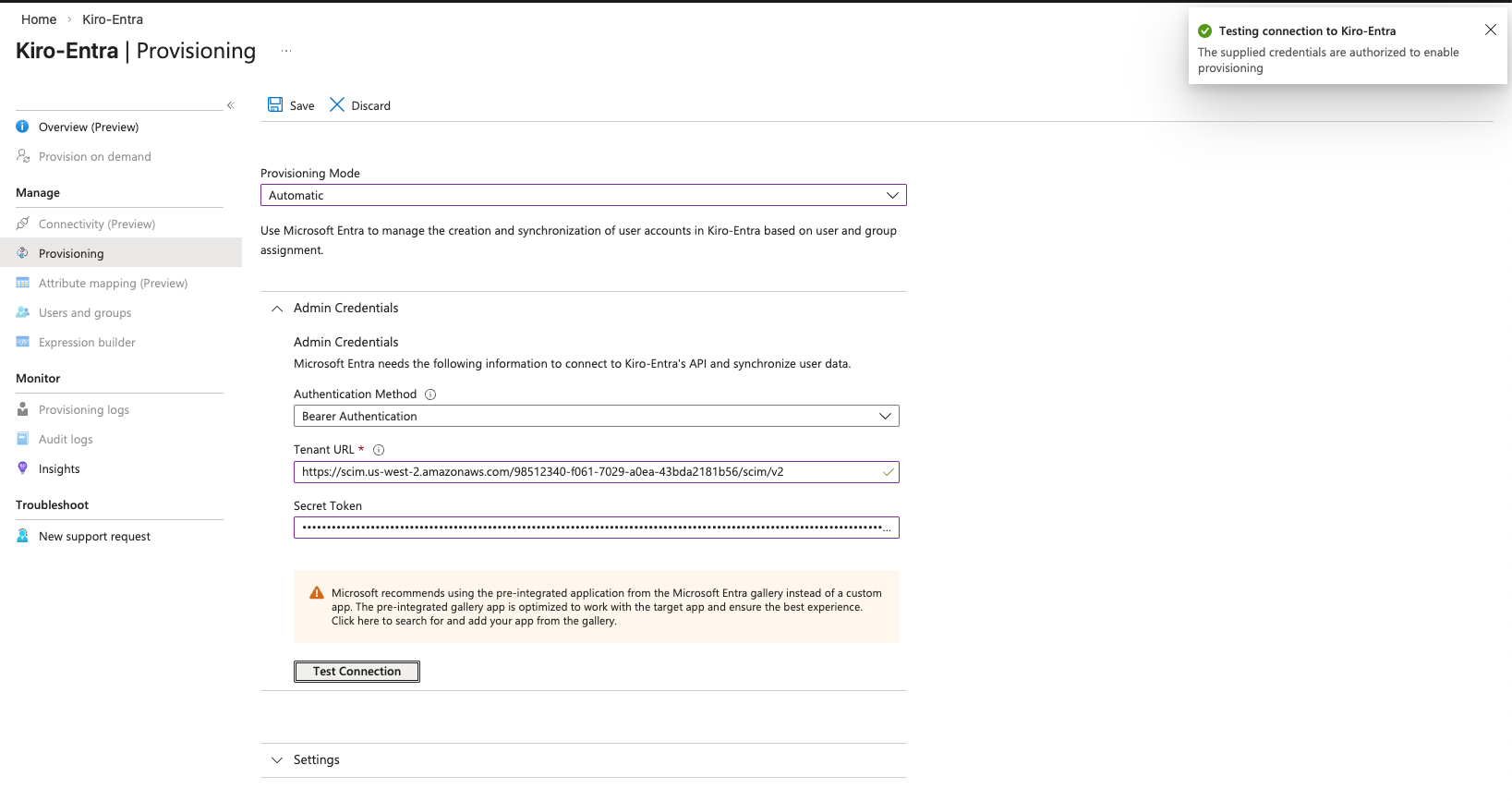
Refresh the application page in Entra ID. The sidebar links should be enabled now. To enable users and groups to be synchronized from Entra ID to Kiro, navigate to the "Attribute mapping (Preview)" section. You will see that both Provision Groups and Users are enabled.
Loading image...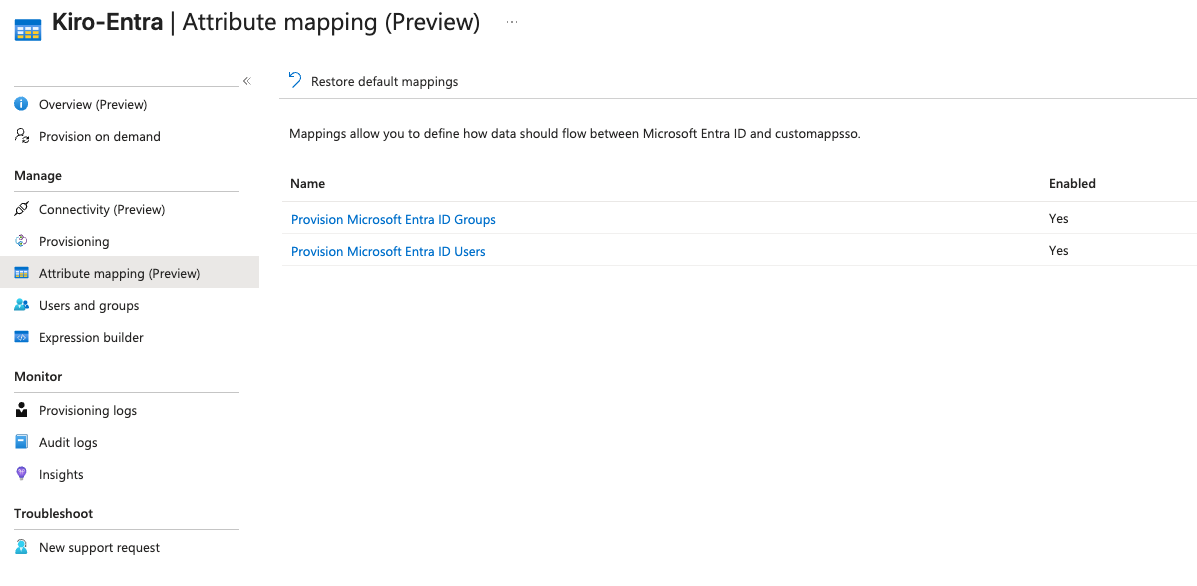
Select the "Provision Microsoft Entra ID Users" link to open the "Attribute Mapping" page. Select the "Edit" button for the "externalId" attribute to open the "Edit Attribute" page. Set the Source attribute value to "objectId" and save the configuration. "objectId" uniquely identifies a user or group and doesn't change, making it easy for Kiro to identify and synchronize users/groups.
Loading image...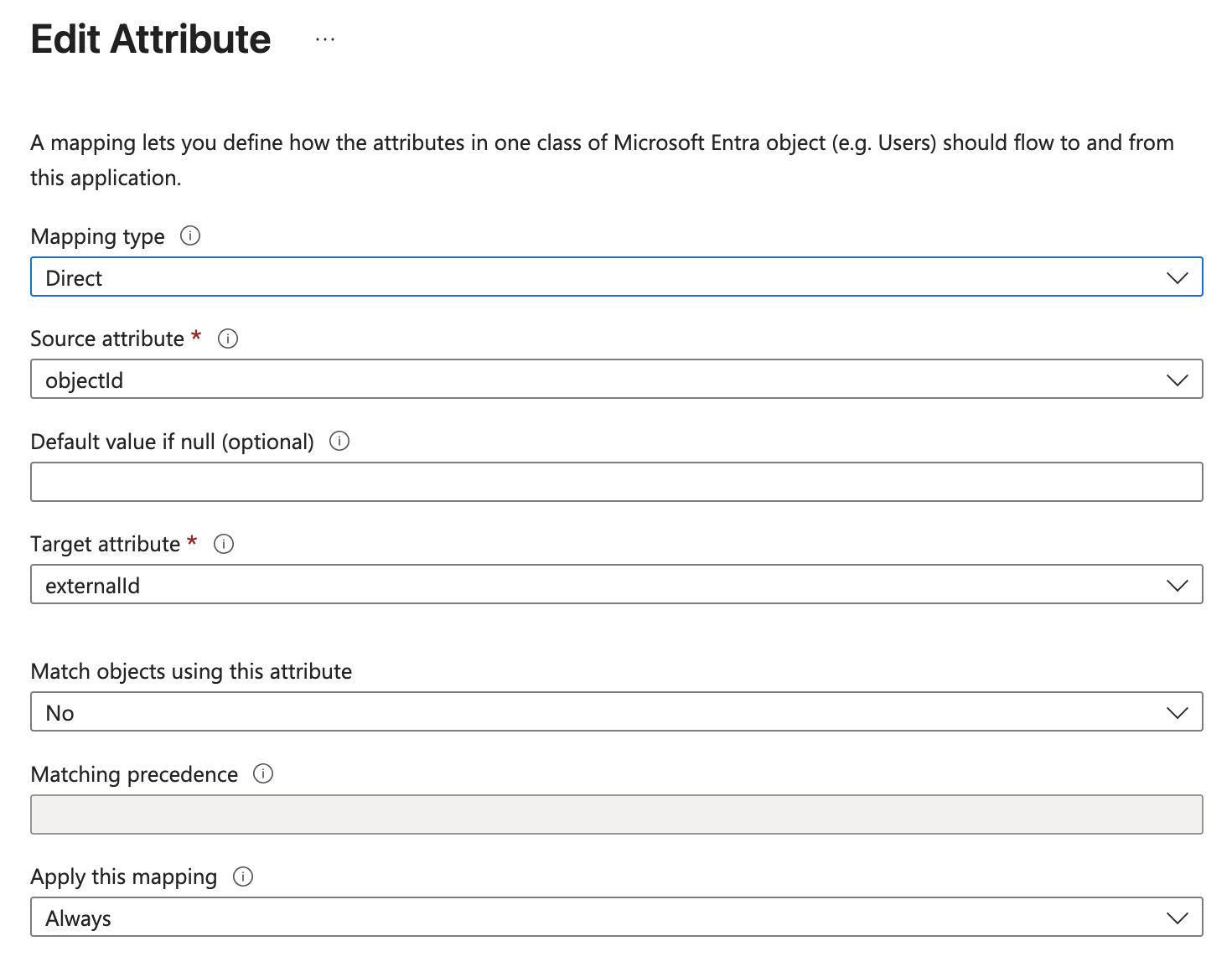
Step 5: Add users and groups
Now that the users and groups can be synchronized from Entra ID application to Kiro, you have to configure which users and groups will be synchronized as part of this application. The selected users and groups will be available to associate with a Kiro subscription in the Kiro profile.
To add users and groups to the application, navigate to the "Users and groups" section in the Entra ID application. Users and groups will appear on their own after ~10 minutes. To manually provision, navigate to "Provisioning" page and select "Provision On Demand" under "Quick Actions" section.
Loading image...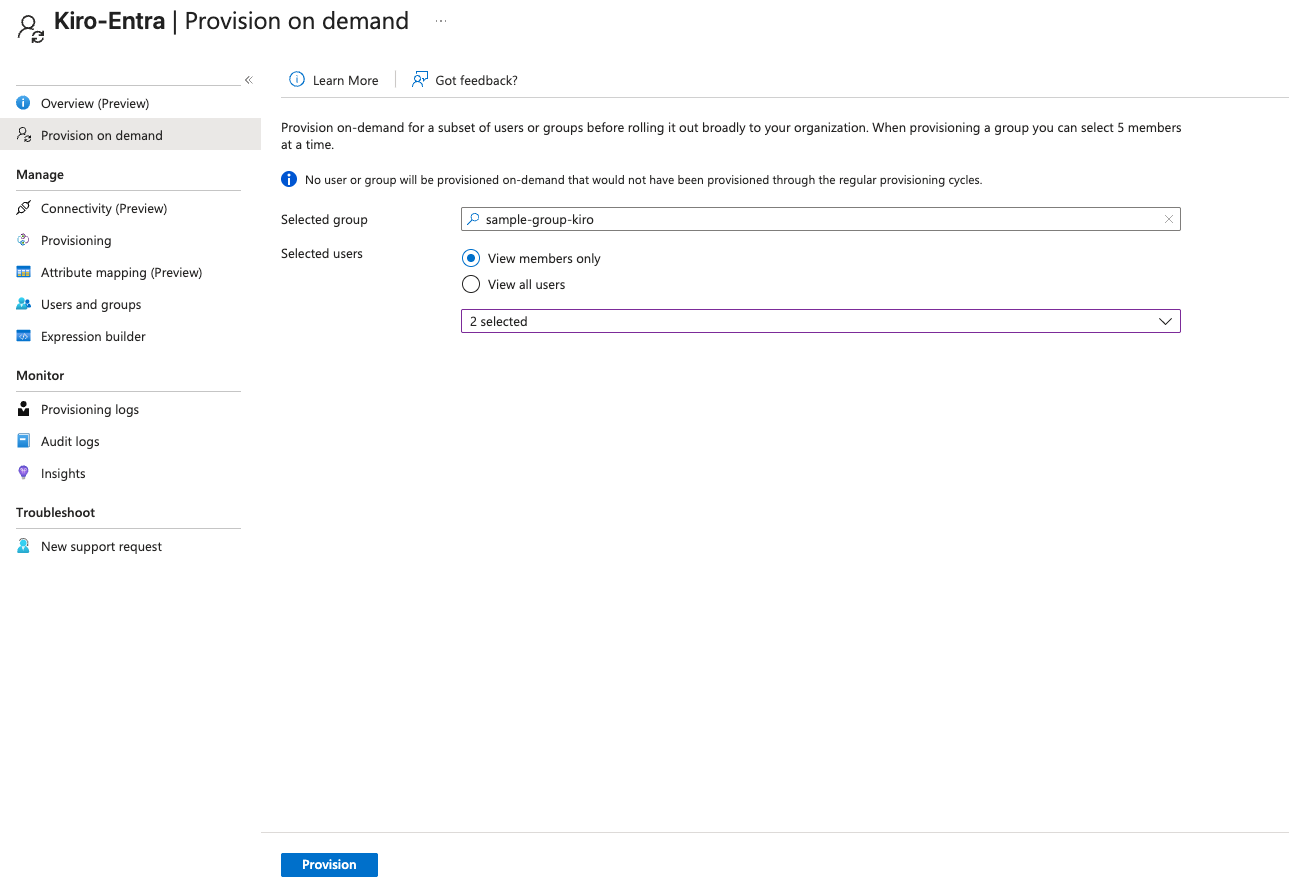
If you are provisioning a group, make sure you select all the users in the group. After you have successfully configured the group and the users in the group, you will see a success screen.
Loading image...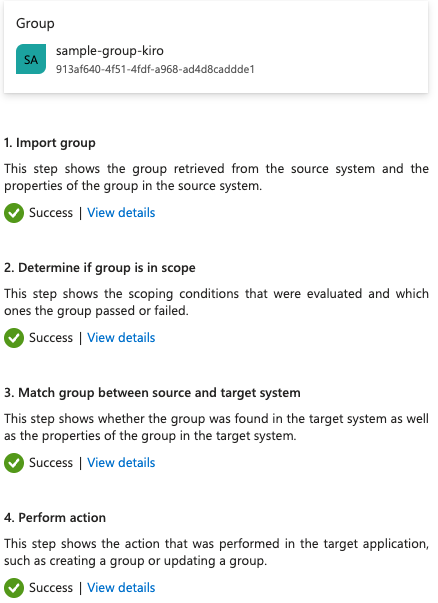
Repeat the steps to add all the users and groups you want to synchronize with Kiro.
You have now completed all the steps required to configure an application in Entra ID, connect the application with a Kiro Profile, and add users/groups to the Profile. You can now start subscribing team members to Kiro.
Page updated: February 12, 2026
Connect your Microsoft Entra ID IdP